Porn Clicker Malware Nesting in Google Play
It’s not the first time Android’s Google Play has been found harboring a malicious application that both hides its presence and performs activities that generate some form of revenue for the attacker.
Last year we not only saw the proliferation of aggressive adware, but also some new CAPTCHA-bypassing threats that subscribed users to a premium-rated number, both hosted in Google Official marketplace.
A new porn clicker malware has been found nested in nine Google Play apps — six have since been removed, but three are still available for download.
How Does the Clicker Work?
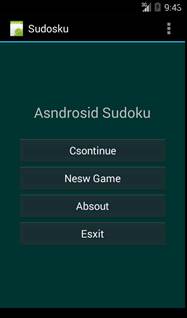
While the applications do perform various clean actions associated with displaying photos with various landmarks around the work or starting a fully functional Sudoku game, what happens in the background is an entirely different thing.
The names of these Google Play applications might not raise any eyebrows of unsuspecting users – Seyrap Tep, Seyran Tep 4, and Sudoku 6 – but make no mistake that, while they might seem to work, they’re true purpose is completely different from what you’re lead to believe.
Fig. 1 – Screenshots with what the user sees in the displayed interface
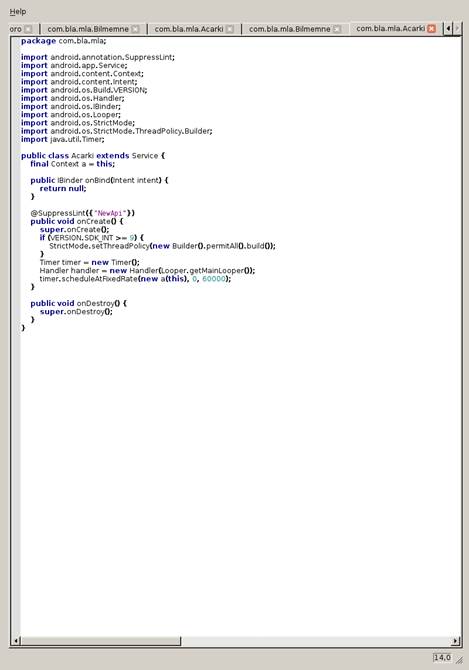
After the apps are launched, they connect to a series of hardcoded websites from which they pull a list of porn sites, without the user suspecting anything. Each link to porn websites parsed from the list is opened in its own hidden window instance, allowing the malware to effectively open porn websites while the user is either playing Sudoku or viewing various images.
Fig. 2 – Hidden window for opening the list of porn websites
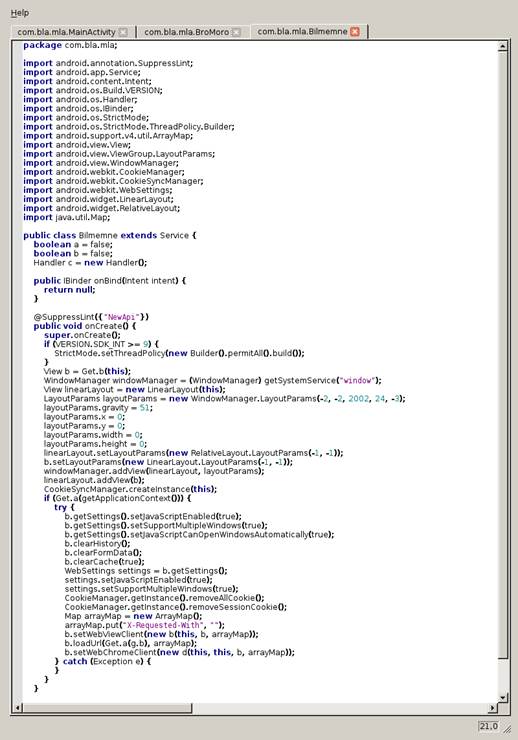
Every 60 seconds a new hidden window – placed outside the visible window of the application – is launched and accesses one of the porn websites in the fetched list.
Fig. 3 – 60 seconds timer loop for starting new services
Here’s the list of apps that – at the time of writing – are still available on Google Play:
| MD5 | Package Name | Version |
| 749ba2d5cacf2f991804ee69afcbcd6b | com.seyran.tep4 | 1.0a |
| b9fa94956f99a8afb8b0a1aba64fdb82 | com.ss.dok6 | 6 |
| cec2e1b08f980d0fab2a916db378505c | com.seyran.tep | 6 |
And here’s the list of apps that have been available in Google Play, but have since been removed:
| MD5 | Package Name | Version |
| 8b69982a787f6b61fcba42c6a00a8c49 | com.bla.mla2 | 1.0a |
| 4ca80d37d962f04e3d1a93264a2a20b4 | com.bla.mla5 | 1.0a |
| 369788c204488eaee731bb68fad73bb7 | com.bla.mla | 1.0a |
| a9e534aeafd2a57311801fecabce7538 | com.bla.mla6 | 1.0a |
| 3996c4a8f09267c02450638ebd58db0e | com.bla.mla4 | 1.0a |
| 5ad5e70cc29cdd38eeb47ac31d881c43 | com.bla.mla3 | 1.0a |
Bitdefender detects this particular form of porn clicker malware as Android.Trojan.Clicker.V.
Implications
The list of address includes 175 porn websites that are constantly visited by infected victims, potentially making hundreds and even thousands of dollars for the malware developers from affiliate fees.
Porn clickers have been known to generate substantial revenue for attackers, especially if they’re downloaded by thousands of users who unsuspectingly click the same ads on porn websites. One of the apps has between 1,000 and 5,000 installs which, for a basic app that simply displays a couple of images (Seyran Tep 4), is quite a lot.
On a more personal note, if you were infected with one of these porn clickers you could end up paying a visit to your local work IT manager to explain why you are browsing so much porn on the company Wi-Fi. You could be considered a future company security risk and lose the privilege of bringing your own devices to work.
Word of caution
While it is true that these applications have been downloaded from the official Google Play marketplace and not some third-party store, average users are highly encouraged to make use of a mobile security solution that can detect such threats.
Also, it’s also advised to check out the app’s rating and comments, as it’s sometimes a good indicator that something might be wrong with app.
At the time of writing, Google has been notified of the existence of these malicious apps in Google Play.