Aussie Android Ransomware Takes a Turn for the Worst
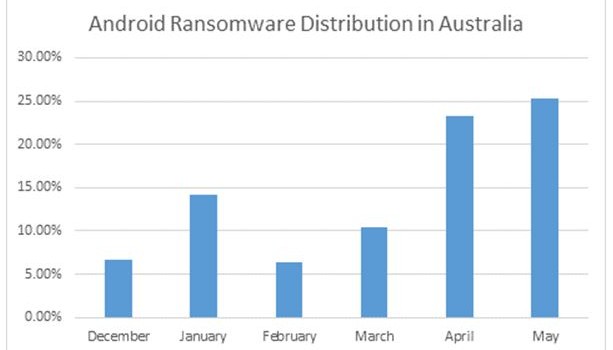
Sydney, 3rd July 2015- In the past six months, ransomware in Australia has seen a steady growth, specifically in April and May 2015. More than 25 percent of all reported malware in May was Android ransomware these numbers are likely tol steadily rise in the next six to twelve months. Considering that in February 2015 the amount of ransomware reported was slightly above 6 percent, this sudden spike translates into an increased interest among cybercriminals in targeting Australia to generate revenue.
Cryptowall ransomware is one of the most prolific and profitable malware strains to-date, causing more than $18 million losses in the past year alone, according to the FBI’s Internet Crime Complaint Center.
Its success in generating revenue has inspired malware coders to now explore new ways of infecting even more victims, by crafting ransomware for Android devices. With Android shipments exceeding 1 billion devices in 2014, it is little wonder the market is sparking the interest of cybercriminals who see it as an environment equally as profitable as PCs.
Practice Makes Perfect
Aggressive and persistent malware doesn’t come out of nowhere. Developing malware involves a similar process to developing software. It takes many iterations and bug fixes until you end up with a really stable build that can perform as expected. The same goes for Android ransomware.
We’ve been seeing Android ransomware samples for the better part of a year now. At first, they had rather limited capabilities. They were mostly designed to scare users into thinking they’re infected by displaying an easily-removable pop-up that contained the same “classic” message as PC ransomware. It only took limited technical knowhow to remove both the pop-up and the application, and users were quick to dispose of them.
For instance, whenever you saw a full-screen message stating that your files had been encrypted and you had to pay a fee to unlock them, all you had to do was hit the “Back” button to exit it.
Unfortunately, malware coders quickly adapted to the mobile operating system platform and began understanding the subtleties of making an application that latches onto the OS tightly, making them both more persistent and scarier for the average user. New Android ransomware can completely block a device’s keys, leaving users with few available options: rebooting or shutting down. Although no actual encryption of local files occurs, the displayed messages try to scare you into paying the ransom.
The latest Android ransomware can only be removed by booting devices in Safe Mode, otherwise it will come back each time your phone reboots. Because Safe Mode booting prevents third-party applications from loading, users can manually uninstall the malware just like any other app.
Word of Caution
Some of the most common attack vectors used for spreading such Android ransomware infections have to do with drive-by attacks or infected applications disseminated through thirs party marketplaces. Consequently, whenever you’re browsing from your mobile device and a pop-up warns you that your device might be infected, don’t download anything that’s not from the official Google Play Marketplace.
If you get infected, we strongly recommend not paying the ransom, as that only fuels the cybercriminal activity. Make sure you always have a mobile security solution installed, as it will detect and report any attempt of inadvertent download or installation of malware.