2010 BSPlayer Exploit Still Affects Current Version: Bitdefender
Bitdefender Research has found that a known and documented buffer overflow vulnerability in 2010 BSPlayer can still affect the current (v2.68) version, allowing arbitrary code execution. Although the POC (proof-of-concept) exploit created in 2010 for the 2.57 had ceased working after the next BSPlayer update, the exploit still manages to crash the application and cause a buffer overflow exception that could allow an attacker to run arbitrary code.
The current version of BSPlayer is used “by more than 70 million multimedia users throughout the world,” according to its own statement, so the current exploit raises the concern that many users might have been affected since 2010.
The Anatomy of the BSPlayer Exploit
BSPlayer contains a buffer overflow in the “bsib.dll” module that can be exploited to achieve arbitrary code execution. When opening an “.m3u” file containing a URL with a large size, the code tries to copy the link into a stack allocated buffer without bounds checking, resulting in a stack overflow. Bounds checking is particularly useful because it’s a method for detecting whether a variable fits into a give type.
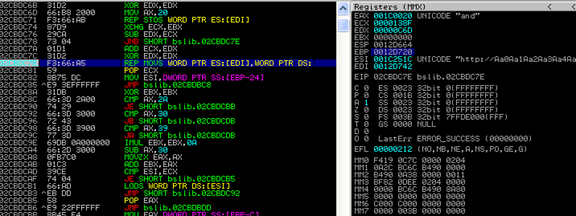
BSPlayer first converts the input buffer into UNICODE[1], making it harder, but not impossible, to exploit.
From the above picture we can see the code tries to copy the input buffer of size 0x138F into a stack allocated buffer of size 0x6CD.
Before the overflow, the stack and SEH[2] (Structured Exception Handler) chain looks like this:
After the overflow, the SEH chain is overwritten with the buffer content. Because BSPlayer is compiled without ASLR[3] (Address Space Layout Randomization) and SafeSEH, we can use an address from the “bsplayer.exe” module as our SEH handler.
The handler allows us to return into our buffer and, using some Venetian shellcode[4], we compute an address to our payload from the EBX register, which points somewhere in our buffer:
When executed, the UNICODE encoded payload will launch “calc.exe”.
The exploit has been successfully tested on Windows XP and Windows 7, both x86 and x64 with the default option of DEP[5] (Data Execution Prevention), which is enabled only for Windows processes and services. However, the exploit doesn’t work on Windows 8 because of the SehOP[6] (Structured Exception Handler Overwrite Protection) protection, enabled by default.
Attack Vectors
Attacks could include everything from maliciously crafted email attachments that rely on user curiosity to be opened and run to ill-intended ads and websites that offer free media content to trick users into downloading and running the “.m3u” file.
In a worst case scenario, once the crafted file runs, it could drop a malicious payload that could be anything from a run-of-the-mill Trojan to full-blown ransomware that can seize critical data and demand a massive payment to access it again.
More skilled cybercriminals would probably consider using this exploit (or any exploit) to infiltrate a computer or network of computers to gain a permanent foothold into an organisation’s network or a victim’s PC. It’s far more profitable to get a constant stream of sensitive or classified information from a compromised computer or network of computer, than to reveal your presence to security software after performing some minor mischief or generating some quick cash by deploying ransomware.
Implications
Anyone with the proper skills might have already weaponised the vulnerability and used it to deliver a malicious payload designed to either recruit a computer into a botnet or deliver data-stealing malware and even ransomware.
Taking advantage of the arbitrary code execution created by the buffer overflow in BSPlayer may allow an attacker to trigger any action he deems fit. In our proof of concept, our actions only cause the calc.exe application to launch, but the consequences could be more dire if the attack were motivated by anything other than scientific research.
Imagine if the first stage in launching an APT (Advanced Persistent Threat) on a large company’s network would be to exploit the weakest link: hitting a company employee with a spear-phishing email. If the email were convincing enough for the employee to launch and execute the BSPlayer .m3u file, his personal computer might get infected. If that piece of malware were to be transported (via USB storage device or other removable storage) onto a company PC, he could attack the company network from within and possibly serve as the first attack platform by exposing the infrastructure to a more potent attack.
Weaponising a vulnerability and using it to serve truly vicious malware is the aim of a cybercriminal looking to either make money or carry out hacktivism. Either way, vendors are strongly encouraged to stay in touch with security vendors and rapidly deploy patches for known critical vulnerabilities. The more popular the software, the more users are potentially exposed.
Exploits – More Valuable than Gold
In 2013, an average of 13 new vulnerabilities were reported per day, while the number spiked to 19 reported vulnerabilities per day in 2014. Clearly, interest in finding new backdoors into popular programs and applications is picking up, leading to an all-out arms-race between vendors and cybercriminals to discover vulnerabilities faster.
In 2014 alone we heard of a plethora of exploits used to deliver malicious payloads. The cybercriminal community is constantly probing Java, Adobe software, and browsers for exploits, because their wide adoption can provide access to millions of victims.
Although Google recently closed down the bounty-hunting program for Google Chrome vulnerabilities, independent security researchers still report major vulnerabilities in popular operating systems or applications, not for money, but out of a sense of morality.
Zero-day vulnerabilities or exploits are potentially damaging because an attacker can inject his own arbitrary code into a seemingly legitimate application and trigger various actions. For instance, he can opt to download additional Trojans or spyware to gain a permanent foothold on the targeted computer and the compromised network.
Secondly, vulnerabilities under the form of buffer overflow errors are hard to control and predict so security solutions often interpret attacker-injected code as legitimate. After all, it has been launched from a perfectly legitimate application.
To this end, zero-day vulnerabilities or exploits are of the highest value to underground markets. They provide a possible means of dodging both security software and other common endpoint security solutions, while surrendering computers to an attacker’s whim.
In recent years, an underground exploit-seeking industry has emerged that has turned into a true cash-cow for black-hat researchers looking to make a quick buck. A single zero-day exploit into a popular application or browser can pay up to six figures, and can reach far more than that if the vulnerability could affect dozens or hundreds of millions of users.
Stay Vigilant
In light of these findings, users are encouraged to always use a security solution that is both constantly updated and able to detect new advanced threats. Even if a cybercriminal can somehow make use of a zero-day vulnerability in an everyday application, a comprehensive and full-fledged security solution will be able to detect the malicious payload served through the exploit. Of course, a top priority should be to install the latest operating system and application updates and patches to minimise risks associated with cybercriminals exploiting known vulnerabilities.
A little caution can go a long way and as such, it is best to avoid opening email attachments from suspect sources or clicking on strange links received either via email or social networks.
Knowledge is the first line of defense against online threats. Exercise a minimum of caution when browser, reading emails or simply operating their PCs.
[1] Unicode is a computing industry standard for the consistent encoding, representation, and handling of text expressed in most of the world’s writing systems. (source: http://en.wikipedia.org/wiki/Unicode)
[2] An exception is an event that occurs during the execution of a program, and requires the execution of code outside the normal flow of control. There are two kinds of exceptions: hardware exceptions and software exceptions. (source: https://msdn.microsoft.com/en-us/library/windows/desktop/ms680657(v=vs.85).aspx)
[3] Address space layout randomization (ASLR) is a computer security technique involved in protection from buffer overflow attacks. (source: http://en.wikipedia.org/wiki/Address_space_layout_randomization)
[4] A technique usually used when dealing with Unicode buffers.
[5] Data Execution Prevention (DEP) is a security feature included in modern operating systems. It marks areas of memory as either “executable” or “nonexecutable”, and allows only data in an “executable” area to be run by programs, services, device drivers, etc. (souce: http://en.wikipedia.org/wiki/Data_Execution_Prevention)
[6] Windows Vista SP1 introduced an interesting new memory protection known as SEHOP, which works with other memory protection techniques (like DEP/NX, ASLR, etc) to help prevent exploitation of a specific type of memory-related vulnerability known as SEH-overwrite. (souce: http://blogs.msdn.com/b/ieinternals/archive/2009/06/18/enhanced-ie-security-with-sehop.aspx)